Ip-com Mobile Phones & Portable Devices Driver
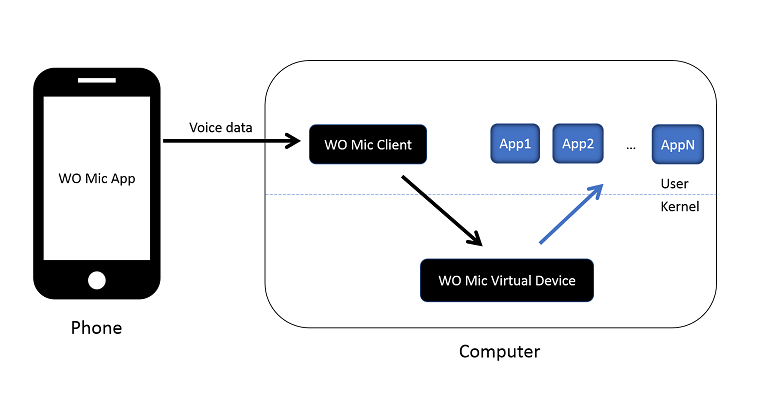
A mobile virtual private network (mobile VPN or mVPN) is a VPN which is capable of persisting during sessions across changes in physical connectivity, point of network attachment, and IP address.[1] The 'mobile' in the name refers to the fact that the VPN can change points of network attachment, not necessarily that the mVPN client is a mobile phone or that it is running on a wireless network.[2]
UKEY mobile identification is unique for each user. You can receive your key remotely (e-mail, WhatsApp, Messenger), saving you time for both the service company and residents. The normal access cards can be copied, so this means that there is a possibility for unauthorized entry into the premises. Style: Smart Mobile Phone, TV Mobile Phone, Business Mobile Phone, Camera Mobile Phone, Music Mobile Phone, Elderly Mobile Phone, Game Mobile Phone; Screen Size: 4.1'-5.0' CPU: Dual-Core 1.4 GHz Cyclone (Arm V8-Based) Operation System: Ios 8, Upgradable to Ios 8.1; Rear Camera Pixel: 8MP. IPCam Pro turns your Windows phone into a IP surveillance camera. Run IPCam Pro on your phone, and via Wi-Fi network, you can view live images captured by your phone's camera. IPCam Pro has professional surveillance features such as motion detection and remote recording. Furthermore, where the agency that controls the IP is located, proxies, cellular IPs, etc. If you are in the US and the controlling agency of the IP is located in Canada. Moreover, chances are the results will show as Canada. Showing a Canadian IP while in the northern US is very common among mobile users on the Verizon network. IP Com Thailand. 1 like 1 talking about this. IP-COM Thailand has been providing commercial networking solutions and high-quality products at disruptive price for SMB and commercial projects.
Mobile VPNs are used in environments where workers need to keep application sessions open at all times, throughout the working day, as they connect via various wireless networks, encounter gaps in coverage, or suspend-and-resume their devices to preserve battery life. A conventional VPN cannot survive such events because the network tunnel is disrupted, causing applications to disconnect, time out,[1] fail, or even the computing device itself to crash.[3] Mobile VPNs are commonly used in public safety, home care, hospital settings, field service management, utilities and other industries.[4] Increasingly, they are being adopted by mobile professionals and white-collar workers.[3]
Comparison with other VPN types[edit]
A VPN maintains an authenticated, encrypted tunnel for securely passing data traffic over public networks (typically, the Internet.) Other VPN types are IPsec VPNs, which are useful for point-to-point connections when the network endpoints are known and remain fixed; or SSL VPNs, which provide for access through a Web browser and are commonly used by remote workers (telecommuting workers or business travelers).[5]
Makers of mobile VPNs draw a distinction between remote access and mobile environments. A remote-access user typically establishes a connection from a fixed endpoint, launches applications that connect to corporate resources as needed, and then logs off. In a mobile environment, the endpoint changes constantly (for instance, as users roam between different cellular networks or Wi-Fiaccess points). A mobile VPN maintains a virtual connection to the application at all times as the endpoint changes, handling the necessary network logins in a manner transparent to the user.[6]
Functions[edit]
The following are functions common to mobile VPNs.[7]
| Function | Description |
|---|---|
| Persistence | Open applications remain active, open and available when the wireless connection changes or is interrupted, a laptop goes into hibernation, or a handheld user suspends and resumes the device |
| Roaming | Underlying virtual connection remains intact when the device switches to a different network; the mobile VPN handles the logins automatically |
| Application compatibility | Software applications that run in an 'always-connected' wired LAN environment run over the mobile VPN without modification |
| Security | Enforces authentication of the user, the device, or both; as well as encryption of the data traffic in compliance with security standards such as FIPS 140-2 |
| Acceleration | Link optimization and data compression improve performance over wireless networks, especially on cellular networks where bandwidth may be constrained. |
| Strong authentication | Enforces two-factor authentication or multi-factor authentication using some combination of a password, smart card, public key certificate or biometric device; required by some regulations, notably for access to CJIS systems in law enforcement |
Ip-com Mobile Phones & Portable Devices Drivers
Management[edit]
Some mobile VPNs offer additional 'mobile-aware' management and security functions, giving information technology departments visibility and control over devices that may not be on the corporate premises or that connect through networks outside IT's direct control.[8]
| Function | Description |
|---|---|
| Management console | Displays status of devices and users, and offers the ability to quarantine a device if there is possibility that it may have been lost or stolen |
| Policy Management | Enforces access policies based on the network in use, bandwidth of the connection, on layer-3 and layer-4 attributes (IP address, TCP and UDP port, etc.), time of day, and in some VPNs, the ability to control access by individual application software |
| Quality of service | Specifies the priority that different applications or services should receive when contending for available wireless bandwidth; this is useful for ensuring delivery of the essential 'mission-critical' applications (such as computer-assisted dispatch for public safety) or giving priority to streaming media or voice-over-IP |
| Network Access Control (NAC) | Evaluates the patch status, anti-virus and anti-spyware protection status, and other aspects of the 'health' of the device before allowing a connection; and optionally may integrate with policies to remediate the device automatically |
| Mobile Analytics | Gives administrators a view into how wireless networks and devices are used |
| Notifications | Alerts administrators of security concerns or connection problems that impact users, delivered via SMTP, SNMP or syslog |
Industries and applications[edit]
Mobile VPNs have found uses in a variety of industries, where they give mobile workers access to software applications.[9]
| Industry | Workers | Applications |
|---|---|---|
| Public Safety | Police officers, firefighters, emergency services personnel, first responders | Computer-aided dispatch, automatic vehicle location, state driver's license and vehicle registration plate databases, criminal databases like the FBI Criminal Justice Information System (CJIS), dashcam software, departmental intranet |
| Home Care | Visiting nurses, in-home physical therapists and occupational therapists, home care aides and hospice workers | Electronic health records, electronic medical records, scheduling and billing applications |
| Hospitals and Clinics | Physicians, nurses and other staff | Electronic health records, Electronic medical records, Picture archiving and communications systems, Computerized physician order entry, pharmacy, patient registration, scheduling, housekeeping, billing, accounting |
| Field Service | Field-service engineers, repair technicians | Field Service Management which can include customer relationship management, work order management, Computer-aided dispatch, and historical customer service data as well as databases of customer-premises equipment, access requirements, and parts inventory; asset tracking, parts ordering, documentation access |
| Field Sales | Sales representatives | Customer relationship management, inventory, order fulfillment |
| Utilities | Linemen, installation and repair technicians, field-service engineers | Computer-aided dispatch, scheduling, work-order management, geographic information systems, maintenance tracking, parts ordering, customer-service, testing and training applications |
| Insurance | Claims adjusters | Claims systems, estimating applications |
In telecommunications[edit]
In telecommunication, a mobile VPN is a solution that provides data user mobility and ensures secure network access with predictable performance. Data user mobility is defined as uninterrupted connectivity or theability to stay connected and communicate to a possibly remote data network while changing the network access medium or points of attachment.[2]
In 2001, Huawei launched a product named 'MVPN'. In this case 'MVPN' had a different meaning from the way that later industry sources would use the term.[10] The Huawei product was focused on delivering a seamless corporate phone system to users whether they were on desktop phones or mobile devices. Although the web page is no longer available, the company advertised that their MVPN had the following advantages over a standard phone system:
- Direct connectivity – the corporate network becomes part of mobile operator's network through direct connection
- Private numbering plan – the communication is tailored to company organization
- Corporate Business Group – all offices and employees are part of one common group, that includes all mobile and desk phones
- Short dialing – a short number to access each employee, no meter on his mobile or desk phone
- Smart Divert – easy divert within company group
- Groups and subgroups – Several sub-groups could be defined within the group with different changing as well as with separate numbering plan
- Calls control – certain destinations could be allowed or barred both on mobile and desk phones.
Vendors[edit]
- Tmharay
References[edit]
- ^ abPhifer, Lisa. 'Mobile VPN: Closing the Gap', SearchMobileComputing.com, July 16, 2006. Accessed July 25, 2009
- ^ abhttp://media.wiley.com/product_data/excerpt/10/04712190/0471219010.pdf
- ^ abCheng, Roger. 'Lost Connections', The Wall Street Journal, December 11, 2007. Accessed July 25, 2009
- ^'Industry Case Studies of NetMotion Wireless Software'. NetMotion. Retrieved 2017-06-07.
- ^'Software Define Mobility'. NetMotion. 2017-06-07. Retrieved 2017-06-07.
- ^Lisa Phifer, Contributor. 'Mobile VPN: Closing the gap'. Searchmobilecomputing.techtarget.com. Retrieved 2014-06-12.
- ^http://www.columbitech.com, http://www.netmotionwireless.com, http://www.radio-ip.com
- ^'NetMotion Software'. NetMotion. 2017-06-07. Retrieved 2017-06-07.
- ^'NetMotion Wireless Customer Case Studies'. NetMotion. 2017-06-07. Retrieved 2017-06-07.
- ^[1]Archived May 25, 2006, at the Wayback Machine
External links[edit]
- 'An Introduction to IPsec VPNs on Mobile Phones' by Ramon Arja, MSDN Magazine, September 2009
- 'Face-off: Mobile VPN is a better choice than an SSL VPN' by Tom Johnaton, Network World (24 November 2006)
BAS-IP UKEY TECHNOLOGY
Use your smartphone instead of access cards!
Learn More
Introducing the UKEY technology
With the BAS-IP UKEY application installed on your smartphone, you can open the doors in a building or receive access to a territory, where the BAS-IP outdoor panels are installed and equipped with an up-to-date multi-functional reader.
Take your mobile phone
Bring it to the panel and activate the telephone screen
The door opens
Usual access cards
How often do you forget to take your access card or keyholder when leaving your house or flat? Meanwhile, your phone is always handy! It is easy to forget your access card, to break or lose it. But you won't forget your phone at home or at work.

It is so easy to forget the access card, you can either break it or lose it. But you won’t forget your phone, either at home or at work.
UKEY mobile identification is unique for each user. You can receive your key remotely (e-mail, WhatsApp, Messenger), saving you time for both the service company and residents.
The normal access cards can be copied, so this means that there is a possibility for unauthorized entry into the premises. However, it is impossible to copy UKEY mobile identification.
If you have lost your card, it could be used by a third party. Telephones have additional face ID/fingerprint or password protection.
Receive the code
Simple and easy access
Activate the screen
Unlocked the screen or just pressed the 'Power' button. Activate your phone, using the 'Raise to wake'.
Using the application
Once unlocked, enter the UI program and open the door by clicking on the button.
The technology is available for different types of buildings
compounds
centers
The equipment supporting the UKEY mobile identification
User-friendliness for all generations
Along with the possibility to open doors and gates via your mobile phone, the system allows using keyholders and access cards of different types of EM-Marin, Mifare.
Ip-com Mobile Phones & Portable Devices Driver
Any questions?
